
Commonly abbreviated as WAF, a web application firewall is used to filter, block, or monitor inbound and outbound web application HTTP traffic. Compared to intrusion detection systems (IDS/IPS), WAFs have a strong focus on the application traffic and have the ability to provide deep data flow analysis. When IDS/IPS serves as a gatekeeper of all network traffic, WAF is only looking for attacks that come from applications, monitoring mostly the HTTP/HTTPS protocol. WAFs inspect the traffic as it comes and goes, preventing common attacks that arise from application code vulnerabilities (such as cross-site scripting (XSS), SQL injection).
For better understanding WAF, one thing you need to know is the nature of the modern network attacks. Most of the successful ones were performed when attackers managed to find a vulnerability in the code and use it to make the malware look like a part of application traffic. As web applications grow in complexity, the need for systems that can decode and analyze HTTP/HTTPS traffic specifically using the wide specter of parameters and behavioral patterns grow. WAF is meant to recognize "healthy" application traffic, pay attention to the weakest points and even help to perform web application security tests, find vulnerabilities in code and patch them on the firewall level. Since WAF precisely monitors application traffic, it also serves as a tool for load balancing and keep-alive optimization.
Another strong benefit of using WAF is having protection against zero-day exploits—that is, a "newborn" malware, which is not detected by any known behavior analysis. It is the most dangerous and popular type of threat that traditional security measures are not equipped to mitigate or prevent.
How do web application firewalls work?
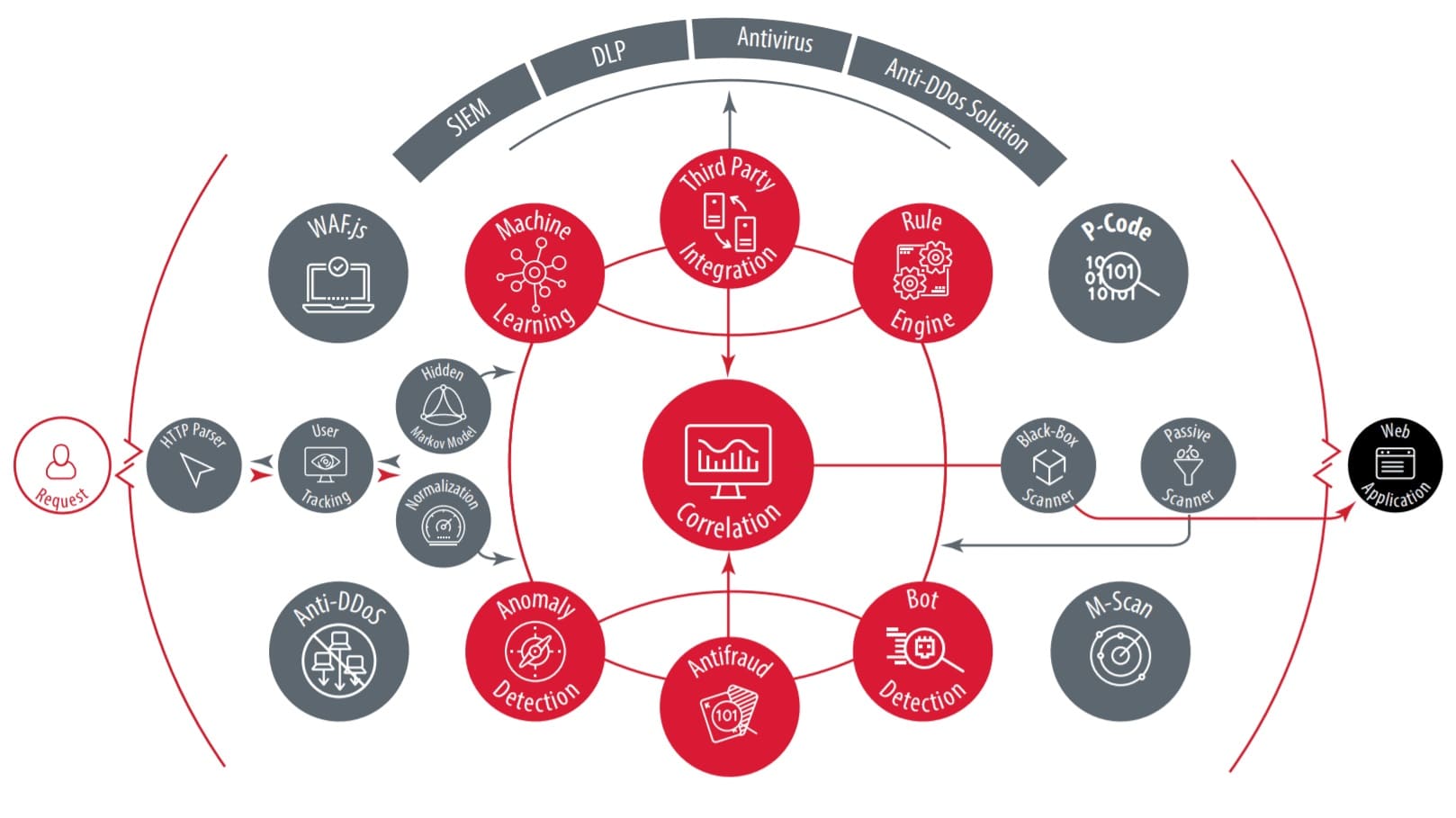
Web application firewalls are designed to be placed on the application layer, acting as a two-way gatekeeper, and analyzes the HTTP/HTTPS traffic going in and leaving the application; the WAF will then take action whenever it detects malicious traffic. A benefit of WAFs is that they function independently from the application, but can constantly adjust to application behavior changes. Thus, introducing a new feature in the application will not result in thousands of false positive threat detections that would have been caused by new data flows.
A WAF can be placed on a dedicated physical server, and although it is often thought of as a stand-alone application, it can also be integrated with other networking components. WAF can be set to different levels of scrutiny, usually on a scale from low to high, and this allows the WAF to provide a better level of security and mitigation for the web application depending on your needs. There is also regulatory standards for WAFs, such as the Payment Card Industry Data Security Standard (PCI DSS) or the Health Insurance Portability and Accountability Act of 1996 (HIPAA).
Analyzing requests and applying filter rules
WAFs use rules and policies to analyze any traffic or requests that contact the web application, make a determination if the traffic is "healthy," and then either approve or deny the malicious traffic flow. Rules and policies are guidelines created to help the WAF make an educated decision; these rules and policies function at a higher level than typical firewall rules and exceptions.
WAFs use layers of filters when analyzing traffic, often checking for zero-day attacks automatically, client-side attacks, bot attacks (for example, DDoS attacks), hidden virus files, and web application vulnerabilities. Most advanced WAFs can decode and analyze HTTPS traffic, XML, JSON, and other popular data transfer formats. It helps them to stop attacks that are meant to go around the firewall, like HPC, HPP, Verb Tampering.
Types of web application firewalls

Network-based web application firewall
Network-based web application firewalls (NWAF) are traditionally hardware based and provide latency reduction benefits due to the local installation. This means NWAF is installed close to the application server and is easy to access. Additionally, NWAFs provide rule and setting replication in many instances, which means that deployment across medium- or large-scale organizations is feasible; cost is usually the most significant drawback.
Host-based web application firewall
Host-based web application firewalls (HWAF) exist as modules for a web server. It is a significantly cheaper solution compared to hardware-based WAFs, which are meant for small web applications. Most of the software WAFs are made to be easily integrated with popular web servers. However, because host-based WAF drains your application server resources, that can result in performance problems. Also keep in mind that some types of web server attacks can bypass WAF and disable its functions from inside — for example, when a malicious file was injected on the server directly through unsecured file transfer channels.
Cloud-based web application firewall
Cloud-based web application firewalls provide similar benefits as other software-based WAF solutions, such as low cost and the lack of on-premises resources that you must manage. Cloud-based solutions are an excellent choice when you don't want to limit yourself with performance capabilities or are aiming to avoid a system that requires maintenance. Cloud service providers can offer unlimited hardware pool with competent setup and support. But at some point, the service fees might grow pretty steep or you will reach the point when you need a powerful custom solution based on your physical appliance.
Blacklist WAF vs whitelist WAF vs hybrid WAF
WAFs can operate under different models, including blacklist (negative security), whitelist (positive security), and hybrid security models.
The blacklist model works by protecting the web application from known attacks or specific signatures; this prevents attacks that exploit these known issues or vulnerabilities. The drawback to this model is that all previous types of blacklists became outdated the moment it was created because of the high percentage of zero-day attacks.
The whitelist model uses signatures as well but also employs logical decision-making and permits traffic that meets specific criteria; this means that requests may be allowed from specific URLs and blocked from all others. The weak point of this model is the additional maintenance that is needed every time you introduce a new application feature. You will probably need to tune the WAF core rules to mark the new application behavior as "healthy" and expand a whitelist.
The hybrid model, as the name implies, utilizes both the blacklist and whitelist models.
Web application firewall vs. network firewall
Choosing between a network firewall and a web application firewall can seem confusing, but there are clear differences between the two. It is important to understand how each type of firewall impacts security and usability in different ways.
Network firewall applications are used to control all the access to local network resources, acting as a gatekeeper between the local network and the Internet. Network firewalls have rules in place that are used to determine which web traffic is allowed. Similar to WAF, these security solutions can come in hardware or software form.
As discussed above, web application firewalls are designed to monitor the traffic going into or coming out of a web app. The illegitimate traffic is inspected individually and then filtered based on whether that traffic is considered harmful or not. With the variable nature of WAFs and the different configurations that can be employed, they are often popular with organizations that provide internet-based services.
Web application firewall vs. intrusion prevention system (IPS)
Web application firewalls and intrusion prevention systems both serve important purposes of digital security — each serves different purposes when it comes to protecting digital assets.
IPS solutions are not designed to have an understanding of the underlying application, which means it is not designed to look for anything that is classified as an attack against the web application; the attack must trigger specific parameters to trigger a response. WAF, on the other hand, is designed to detect and prevent different attack styles against a web application, but, unlike IPS, they do not just purely review all the traffic that occurs.
Any organization that already has an IPS should consider implementing a WAF to complement the security solution.
Web application firewall benefits and concluding thoughts
Web application firewalls provide an intelligent response (based on web security settings) to potential threats that can impact your network. WAFs are designed to help protect your network from potential threats that have yet to be identified, which means that implementing this solution can save your organization from zero-day threats, security vulnerabilities, SQL injections, cross-site scripting attacks, and other types of threats.
Well-developed WAFs also engage in mitigation actions when bot attacks or excessive traffic events occur. WAF will keep "clean" application traffic while simultaneously defending all the malicious data flows.
Maximize innovation with PT AF

Positive Technologies Application Firewall (PT AF) maximizes innovation for your security needs, providing protection that dramatically exceeds standard WAFs. PT AF utilizes machine learning to proactively protect web applications from a variety of attacks, both expected and unexpected. Through continuous updates based on security research and logical analysis of attack attempts, PT AF responds to and mitigates zero-day attacks, DDoS attempts, XSS attacks, and other vulnerabilities and weaknesses. Additionally, PT AF automatically creates virtual patches to address identified vulnerabilities without user intervention; this allows PT AF to respond to threats quickly and efficiently without human interaction or intervention. PT AF is designed with over 15 years of in-depth security research. The culmination of this research provides top of the line security response, and it is constantly updated by Positive Technologies to make sure that new threats are integrated to give the firewall more countermeasures and threat detection standards.
PT AF — Web Application Firewall
Our web application firewall is an innovative protection system that detects and blocks attacks including the OWASP Top 10, WASC, layer 7 DDoS, and zero-day attacks with pinpoint accuracy. It ensures continuous security for applications, APIs, users, and infrastructure while supporting compliance with security standards including PCI DSS.

