Positive Technologies has unveiled PT Network Attack Discovery (PT NAD) 10.3, the latest version of its network traffic analysis (NTA) system for detecting attacks on the perimeter and inside the network. Among the major innovations are detection of slow network scans and unauthorized connections, and parsing of the VXLAN and Geneve tunneling protocols. These new features identify cybercriminal activity in the early stages of an attack.
Detection of new threats
PT NAD 10.3 detects new nodes in the network, which in turn helps to find threats in segments of the corporate network where they rarely occur.
"The system is self-learning, which means the analysis excludes network segments where new hosts appear as part of the workflow. For example, guest Wi-Fi or a test segment. If an unknown PC appears in the accounting or development department, PT NAD sends a notification. Such incidents can occur in large companies and are listed in the MITRE ATT&CK threat matrix," notes Dmitry Efanov, Head of PT NAD Development.
Starting with this version, the product has the capability to detect slow scanning. Slow scanning is deployed by attackers to make it difficult to detect network reconnaissance. In practice, an attacker can analyze the network over a 24-hour period, sending a minimum number of packets per unit of time. Such activity tends to escape the attention of monitoring tools, but the new PT NAD identifies scans distributed over time.
PT NAD 10.3 now detects NTLM-Relay attacks as well 1. These are effective man-in-the-middle (MITM) attacks in which an intruder interferes with NTLM authentication between the client (victim) and the server. Successful implementation results in server access with the privileges of the compromised user. In this way, an attacker can perform lateral movement in the network and gain access to critical systems, such as a domain controller.
In addition, a listing of user sessions has been added to the PT NAD 10.3 activity stream. In other words, it is now easier for an infosec expert to detect attacks to steal information about users authenticated on a host.
PT NAD’s new functionality has already been evaluated by CyberART, the cyberthreat prevention center of Innostage Group. The Innostage team was responsible for Security Operations Center (SOC) monitoring at The Standoff, which took place on May 16–19, 2022, as part of the Positive Hack Days 11 practical cybersecurity forum:
"PT NAD 10.3 formed part of our SOC toolkit for monitoring the cyberbattle," says Anton Kalinin, Head of CyberART. "The system has enough information dashboards to analyze the overall situation in the infrastructure. By analyzing node interactions in the network on the ’session’ and ’attack’ pages, you can collect a large scope of information about targeted attacks. The common filters update makes it possible to upload files that were detected in traffic, including setting up a native integration with PT Sandbox and configuring file verdicts in PT NAD."
Enhanced UX
As for changes in the system interface, the product can now perform operations on multiple activities at once: enable/disable activity tracking or undo a previous action.
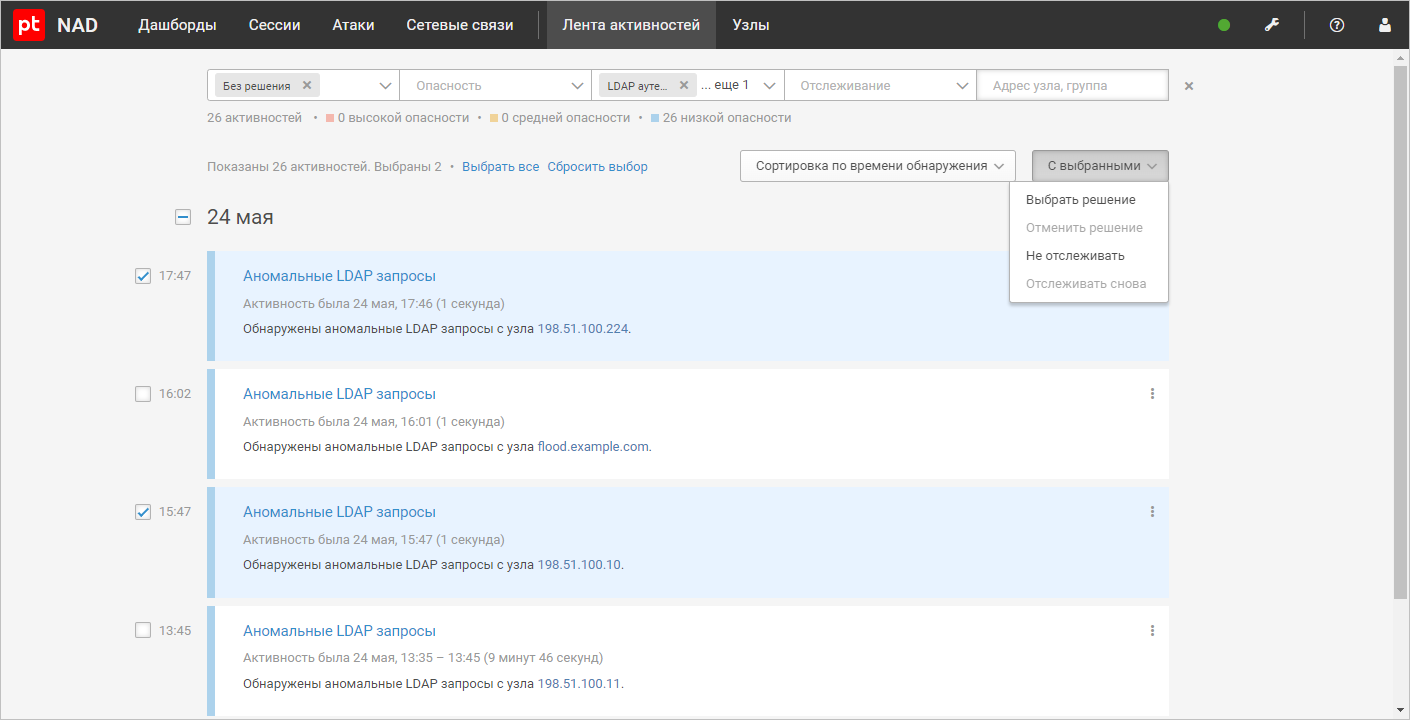
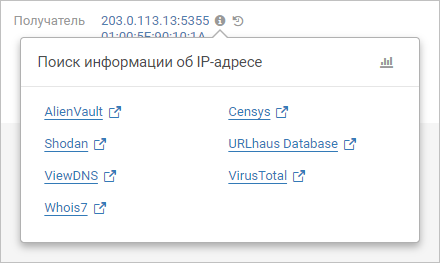
Another innovation is that operators can quickly switch to viewing information about IP addresses, domains, and files involved in network interactions from the interface page where they are displayed.
Also new in version 10.3, operators can configure searches for dangerous or potentially dangerous activities.
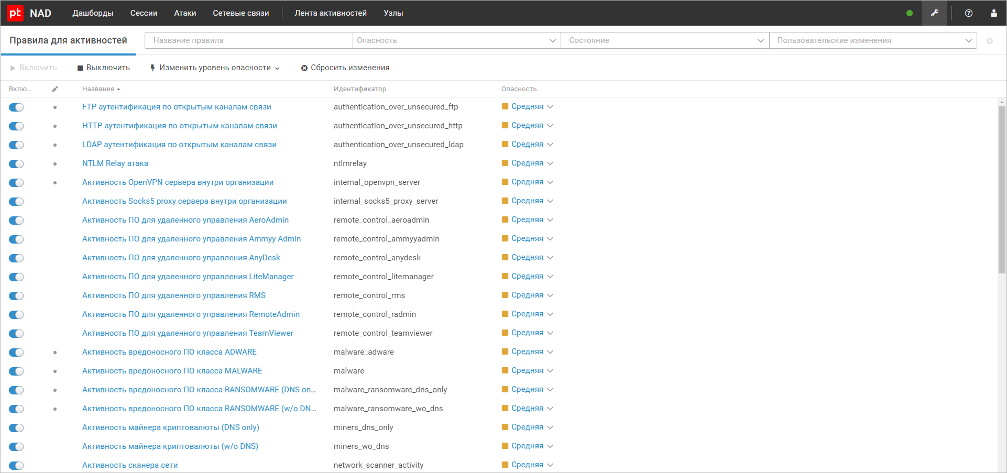
In terms of usability, PT NAD 10.3 has become simpler: now infosec experts can detect and localize an attack by taking the standard actions recommended in the Positive Technologies Expert Security Center (PT ESC) knowledge base.
Another important addition is the change in how rules and reputation lists are loaded from the PT ESC knowledge base. It is now possible to set up a local mirror of the Positive Technologies public server with updates, so that PT NAD can receive updates while running in an Internet-isolated network segment.
Other improvements in version 10.3 include detection of new protocols in traffic, such as Lotus Notes, WireGuard, and Redis, and parsing of the VXLAN and Geneve tunneling protocols.
PT NAD 10.3 is already available to users. Apply for a free pilot here. Existing users can upgrade the product version from the PT NAD knowledge base.
- Attacks on protocols that support NTLM authorization (SMB, HTTP, LDAP, etc.)
