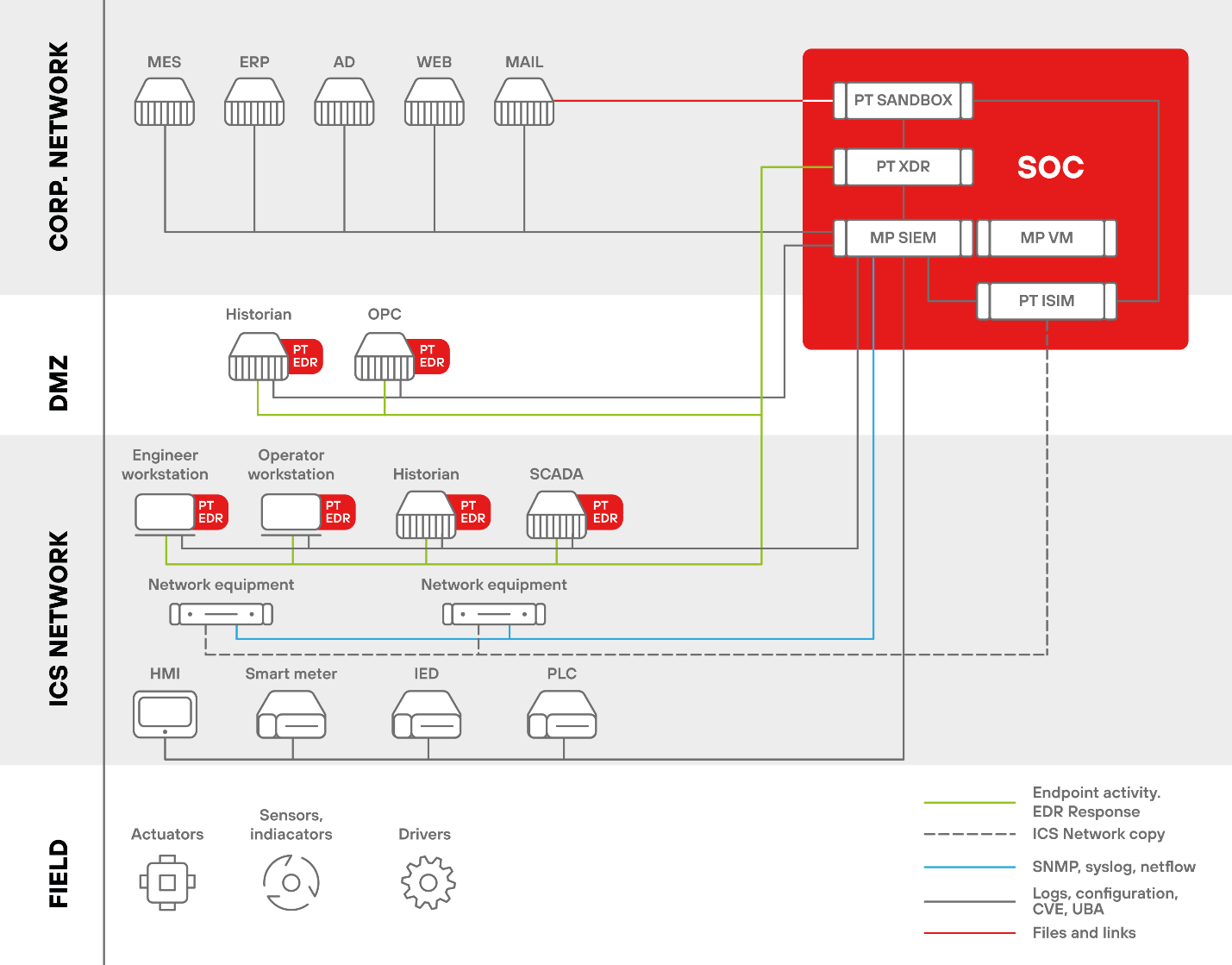
PT Industrial Cybersecurity Suite is the first integrated platform to protect industrial systems from cyberthreats. It helps identify attacks at any stage in an industrial environment and respond to them swiftly. PT ICS provides comprehensive security for industrial systems, covering everything from network hosts to individual devices.
Overview
PT ICS components
1. MaxPatrol SIEM for industrial systems
Detection and management of cybersecurity incidents in industrial infrastructure. Out-of-the-box support for common SCADA components.
2. MaxPatrol VM for industrial systems
Automated vulnerability management in industrial infrastructure. Out-of-the-box support for common SCADA components.
3. PT ISIM
Deep analysis of ICS network traffic. Threat hunting tools, automated attack vector identification, and retrospective network analysis. Supports more than 120 network protocols.
4. PT Sandbox for industrial systems
Detection of unknown ICS/SCADA malware. Customizable emulation environment with deception mechanisms allows deployment of industry-specific software.
5. PT XDR for industrial systems
PT XDR provides endpoint detection and response (EDR) agents specially adapted for operating in industrial environments. The EDR agents gather and analyze data from network endpoints to assist in hunting and neutralizing cyberthreats.
PT ICS services
PT Industrial Cybersecurity Suite is more than just a combination of flagship Positive Technologies products. It offers a comprehensive package of ICS/SCADA security assessment and forensic investigation services in order to discover, investigate, and respond to complex incidents in industrial systems.
End-to-end information security management
Resources
►

