The 12th edition of Positive Hack Days, which was organized in Gorky Park by Positive Technologies, leaders in results-oriented cybersecurity, has come to an end. This year, the event reached a new level, transforming into a large urban cyberfestival. The main aims were to increase trust in technologies and promote awareness of their use through cyberawareness. The fact that a wide range of users, business representatives, government officials, and the media showed interest in the event emphasizes once again how information security is a matter of pressing concern for everyone today.
Visitors to the open space of the cyberfestival—the cybercity—learned how to avoid becoming victims of scammers on marketplaces, as well as how to use ChatGPT for cybersecurity purposes, how to choose a secure VPN, and other aspects of IT and information security. During the cyberfestival's conference section, experts discussed the transition of government agencies and private companies to results-oriented security, strategies for bringing the community together, secure development methods, and the growth of the bug bounty market. The Standoff cyberbattle ended after four days of intense struggle in the fictional State F (with real control and defense systems). The attackers managed to trigger non-tolerable events 204 times, while the defenders investigated 43 attacks. If the cybersecurity professionals who participated in the battle are faced with similar malicious activity in their own companies, they'll now be prepared to respond effectively.
Guaranteed protection as an end result: who's responsible for it?

The topic of results-oriented cybersecurity was still front and center during the conference section of the second day.
Vladimir Bengin, Director of Cybersecurity was amazed by the packed audience on Saturday morning. He reminded everyone that cybersecurity specialists have to take direct responsibility for their results.
"We were waiting for the business world to listen to us, and now it has listened. Companies don't care which security measures are implemented; they care about results and understanding who is responsible for those results. Unfortunately, security experts are often unable to explain what the results will be. Deploying some popular security system is not a result. A real result is when a security specialist informs management that specific vulnerabilities in the company are currently being eliminated, say, within 127 days, and that this is too risky: they must be eliminated within 12 hours in critically significant segments, and this will require so many million rubles," Vladimir Bengin admitted.
Aidar Guzairov, CEO of Innostage (co-organizers of Positive Hack Days 12), said that the changes that have taken place over the past year in terms of goal setting, awareness, and everything else that is happening in the cybersecurity space are comparable to a five-year period in calmer times.
"Two years ago at PHDays, we talked about how great it would be if executives started to think seriously about information security. Well, be careful what you wish for: now many managers have gained first-hand experience of the importance of information security. On the other hand, the question of who is responsible for results is now understood differently in the cybersecurity industry. If two years ago I could only call our company an "integrator," now we are much more than that: now we're responsible for the results, for ensuring that hackers do not threaten our clients' business. For us, our risks are primarily reputational. We're starting to think about how to achieve results in the cybersecurity field in a different, more effective way," Aidar Guzairov emphasized.
Sergey Sherstobitov, CEO of Angara Security, agreed with the idea that the Russian cybersecurity space has undergone five years' worth of change within a single year. He noted that domestic developers are the ones benefiting most from the current window of opportunity.
"A lot of interesting products are emerging. Clients are moving towards using services. If previously we only discussed how information security services can deliver great results in a reasonable timeframe, now services are becoming in demand in almost all areas. The only exception is insurance services, which for some reason are not taking off," said Sergey Sherstobitov.
"The biggest change in the last year is the new attitude of company owners towards information security issues," said Pavel Kulikov, CTO of CDEK. "Many organizations have been hacked, resulting in a shift from the paradigm of 'cybersecurity is about continuous improvement and training' to a focus on concrete results. Having companies on the Russian market that can deliver results immediately, rather than after six months or a year, is good news. When we were faced with the task of protecting our email, we connected to the service within three days, while by ourselves it would have taken us 3.5 months to prepare for such work, according to our initial estimate. But in the current circumstances, we don't have that time. We are transitioning from perpetual continuity to being more concrete."
About bug bounty as an element of results-oriented security

We can't talk about results-oriented cybersecurity without mentioning bug bounty programs; over the past year, these have been widely talked about. The specific results that can be obtained using such programs were discussed during the business section of the cyberfestival.
Vladimir Bengin, Director of Cybersecurity at the Russian Ministry of Digital Development, noted:
"A bug bounty is an excellent way to stress test a huge number of your organization's internal processes. We launched a program on two commercial platforms at once—Standoff 365 and BI.ZONE Bug Bounty. In general, we were confident in the security of Gosuslugi: our systems have been pentested by almost every Russian cybersecurity company. In total, about 8,000 people participated in our bug bounty program. Hundreds of reports were submitted on both sites, resulting in more than 30 confirmed vulnerabilities. Critically dangerous flaws were also found. The maximum reward was 350,000 rubles. In the future, we will think about how to scale this experience. For a company or organization wanting to test its security, there's nothing cheaper and more effective than a bug bounty program."
According to Alexander Khamitov, Head of Application Security at Wildberries, the bug bounty community not only checks for vulnerabilities, but can also come up with interesting ideas.
"We received unexpected proposals from bug bounty participants to organize testing virtually from specific order collection points," said Alexander Khamitov.
At the same time, many organizations are still in no hurry to launch a bug bounty.
"Some information security specialists may believe that they already know all of the vulnerabilities in their company's systems, so they postpone bug bounty testing. Other organizations may think that if you launch a program, you will have to admit that there are holes in your security. Management may treat vulnerabilities as a failing of their security department and take measures accordingly. There's probably also an unfounded fear that a bug bounty could be exploited by black hat hackers. In fact, the reverse is true: bug bounty lets you monetize vulnerabilities within a legal framework so that people don't try to sell information about them somewhere on the dark web. My opinion is that participating in a bug bounty program is an absolute must," said Dmitry Gadar, Vice President and Head of Information Security at Tinkoff Bank.
Ilya Safronov, Director of Infrastructure Protection at VK, agreed with his colleague:
"We are a mature IT company, so we had no fears about participating in a bug bounty program on the Standoff 365 platform. Of course, it's not very pleasant when you think you've checked everything in terms of vulnerabilities, and then a bug bounty discovers a bunch more. But if a company has three releases a day, it's impossible to completely check everything right away. Bug bounty programs help a lot in this regard."
Experts noted that bug bounty is a continuous process, which gives it an advantage over, for example, pentesting. Pentest results become obsolete the same day the test ends: the infrastructure changes, new security gaps appear, there is shadow IT in operation that the company is not aware of. With bug bounty, you pay for the result in the form of discovered vulnerabilities rather than the service; however, it's not a silver bullet—it's just one of the tools in the security check kit.
"It's not known what's happening inside the infrastructure, and it's not necessary that all vulnerabilities are found as part of a bug bounty. That's where the SOC comes in. By the way, in our company, every discovered flaw is checked: why the WAF wasn't set up properly, why the AppSec team didn't find the vulnerability in the early stages using the appropriate instruments, and so on. We review the entire chain and try to eliminate security flaws in the future," Dmitry Gadar explained.
Community and the methodology of results-oriented information security

Another topic covered during the cyberfestival was the role the community plays in shaping results-oriented security approaches: a platform was presented on which the community can bring together frameworks for building results-oriented security. The open community rezbez.ru was created for information security experts, allowing them to exchange knowledge and experience with a focus on achieving practical results. To ensure a high level of cyberresilience, the platform will take an integrated approach based on 10 domains covering different areas of information security. Implementing the steps and practices proposed in each of the domains will not only help businesses to comply with regulatory requirements, but also encourage them to confidently develop in the digital space. In the coming days, more methods and recommendations, templates and examples, checklists and other useful materials will be added to the site.
The discussion participants agreed that the community needs such a platform, and that vendors should take responsibility for the creation and development of such platforms. At the same time, to attract experts, it's important to ensure the transparency of their work in terms of intellectual property rights, and at the first stage financial incentives are likely to be needed.
Roman Chaplygin, Director of Business Consulting at Rostelecom-Solar, noted that results are required in various aspects of cybersecurity, including processes, and that the community needs to learn that goal-setting should be done with results in mind.
Sergey Gordeychik, CEO of CyberOK, said that any activity should be measurable:
"The issue of security measurability and security metrics is always relevant. Therefore, if you're initiating some kind of activity in the field of information security, you need to understand what the aims of that process are and how you will track its progress."
A number of the participants reported that, in Russia, there are no systematically built and organized platforms for the community like the ones in the West. Nevertheless, there are developments which should be worked on and systematized in some way. According to Andrey Yankin, Director of the Information Security Center at Jet Infosystems, between "a bunch of muted telegram channels" and overregulation, there is a lack of an open platform where ordinary specialists can communicate freely.

The past year has demonstrated that cyberattacks can only be resisted in a collaborative effort. However, despite the participation of representatives from many companies in the so-called operational headquarters created to counter cyberthreats, not all players in the domestic cybersecurity market are willing to share their best practices. Attack indicators, signatures, and correlation rules are just a few of the things that companies keep to themselves, preferring not to share with the community.
Nikolay Arefiev, CEO and co-founder of RST Cloud, explained why companies are unwilling to share indicators of compromise:
"Technically, you could share indicators of compromise, but there would be problems regarding the context. As a rule, organizations themselves manually collect, clean, and enrich the data. The result is that it's probably possible to give the actual indicator, but real labor costs in terms of human resources and company money were invested in its creation. How to share this is an open question."
In turn, Vladimir Dryukov, Director of the Cyberattack Monitoring and Response Center at Rostelecom-Solar, drew attention to the moral and ethical aspects of a company publishing its work:
"Now everyone is being attacked through Exchange. I consider it my social duty to share rules for detecting cyberthreats rather than waiting for customers to get hacked."
According to Teymur Kheirkhabarov, Head of the Cyber Defense Center at BI.ZONE, a standard is needed that will encourage Russian security vendors to share information with the cybersecurity market more often:
"The standardization of protocols, interaction interfaces, data exchange formats—we're really lacking this. Each vendor creates the API in its solutions as it wants; everyone has their own formats and rules. It's simply impossible to work together in the absence of standards."
Andrey Yankin, Director of the Information Security Center at Jet Infosystems, added that in order to cooperate, a platform that can bring together information security companies is required.
"For many smaller players, this would give them the opportunity to join the river of cybersecurity and quickly start helping each other. This platform should not be about competition," he said.
Sergey Soldatov, Head of Kaspersky's Cybersecurity Monitoring Center, spoke about how there could be bureaucratic barriers on the way to creating such a platform, and that the state should play a major part in facilitating communication between organizations.
On high tech development, DevSecOps, and outlook for domestic operating system

The future of the high tech industry was discussed by development directors and business co-owners. Foreign vendors' exit from the Russian market has created opportunities for breakthroughs in various technology segments. Monopolists who had held their niches 100% are now gone. But the users are still there, expecting the same level of products and services as before.
"The first technological leap the domestic industry needs to make—and quickly, too—is to ensure software production and maintenance at the same level offered by foreign vendors," says Alexey Totmakov, CTO at VK Tech.
Konstantin Osipov, co-founder of Picodata, named SCADA and ERP systems, databases, and computer aided design (CAD) systems among the priority segments for import phase-out.
There is also the fundamental need for open processor technologies and their implementation based on open standards.
"We need to invest into open-source hardware design—currently these are monopolized by non-Russian vendors," comments Igor Lopatin, R&D director at Yadro Research and Development Center.
As the second important investment vector, he named funding that would allow vendors to write optimized libraries and "other building blocks for these processors, which will add up to a software ecosystem for the new open architectures." Igor was moderately optimistic about the outlook for domestic hardware, but he stressed that we can hardly expect quick wins in CPUs, which are extremely sophisticated components.
"There are areas that Russian vendors had stayed away from knowingly as they had no experience in engineering. Now that foreign players are gone, we'll just have to enter these areas out of necessity," says Alexey Andreev, Managing Director at Positive Technologies. "On the other hand, the vacated niches will be taken by domestic vendors. In particular, I am referring to the network security segment and the next generation firewall niche. In areas where we have complementary expertise, we are in for technological breakthroughs."

In 2022–2023, the topic of DevSecOps grew even more popular, and the user portrait changed.
According to Denis Korablev, product director at Positive Technologies, the DevSecOps topic is now much more popular than a year earlier.
"Many western vendors having left the Russian market, various products had to be developed from scratch. I am happy to see that most vendors have security in focus from the outset, building it into their production workflow. Truly a big difference from what we had before. Given the current situation and the number of attacks across the board, people just cannot ignore security when choosing their approaches," the expert believes.
Rami Muleys, security product manager at Yandex Cloud, has noted a triple increase in the number of users of the DevOps management platform GitLab within the Yandex Cloud infrastructure. According to him, partial withdrawal of western vendors has made development more difficult:
"Things are greatly complicated by the fact that there are progressively fewer out-of-the-box solutions for DevSecOps. We see that the stake is on open source security solutions."
According to Yury Sergeev, founder and managing partner of Swordfish Security, it should be remembered that all vendors using open source solutions become responsible for the security thereof.
Following the exit of foreign vendors, the situation in the field of domestic OSs has changed, too: vendors feel assured of their prospects and identify new opportunities. Thus, according to Vladimir Telezhnikov, Head of Scientific Research at Astra Group of Companies,
"it wasn't all easy, but the company has recovered from stress and is now comfortably pursuing product development, making headway: we have accumulated good deployment experience and positive feedback from our users."
Roman Alyautdin, Head of Development, Aurora OS (Open Mobile Platform), is assured that Russian operating systems are going to be a success:
"Russian vendors have laid a solid foundation on which to build their ecosystem, while competing in the market—including with technologies the market has trained us to consume. We have everything we need for that: people, technologies, expertise."
Cybercity: park visitors learning about ChatGPT features and how not to fall victim to scam

A space open to all the Gorky Park visitors (PopScience track) provided a setting for a discussion of things all people feel keenly about. Retail representatives covered symptoms that indicate an unreliable online store. CDEK CTO Pavel Kulikov recommended users to avoid taking their communication with sellers to third-party platforms when negotiating deals at marketplaces, as this is what scammers use a lot.
"During the pandemic, many retailers were unable to process the influx of orders, which created an opportunity for rogue actors, who would build fake or go-between websites, for example, guised as the Azbuka Vkusa supermarket. In the best case scenario, the clients would end up paying more for what they got; in the worst they would see neither their stuff nor money. Check the site you are going to use for payment—at least by verifying the legal entity's bank credentials that legal websites always provide," was the advice given by Dmitry Kuzevanov, technical director at Azbuka Vkusa.
Valentin Malykh, an NLP researcher at Huawei, spoke about the inner works of ChatGPT—a system under the influence of which hundreds of western experts, including Elon Musk and Steve Wozniak, demanded that rules for intellectual assistants must be enforced.
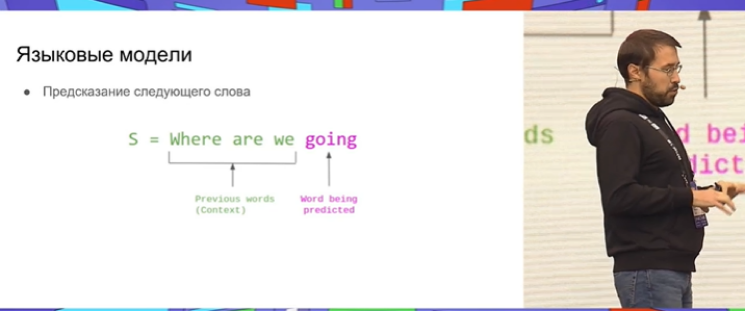
"ChatGPT is all over the place for the past six month, so let me try to explain how the technology works from the inside. The term NLP is about how we communicate with texts. Each one of us has a language model that helps us to get our thoughts across. The most basic definition of language relates to, so to say, a "prompt" that makes one arrive at the next word. If someone opens with "better late," everybody's ready response will be "than never." ML assistants employ exactly the same next word generation models—only thousands of times more sophisticated," Valentin Malykh said.
Egor Bayandin, CIO and co-founder of Whoosh kicksharing service, spoke on whether scooters can collect environmental and user data, and whether scooters can be hacked to remotely control their speed and other parameters. According to Egor, scooters know almost nothing about their riders. Moreover, during the service's four years of operation, users' data were never stolen. The expert also warned on the importance of physical safety when using scooters, in particular the imperative that one scooter must never be used by two riders together. He explained that even motorcycle riders are at risk of accidents due to improper actions of their passengers.
Yana Yurakova (Positive Technologies Senior Information Security Analyst) and Sergey Polunin (Gazinformservis) spoke on how to choose a secure VPN service, the technology being in great favor due to blocking of resources. According to Yana, confidential data leakages can occur only from VPN services owned by unscrupulous persons, and if connection is established through the non-secure HTTP protocol (lacking the little lock icon in the browser). Sergey pointed out that VPNs are expensive to maintain, and one should analyze the monetization model used by the free ones to figure out what the user is going to pay with (ads or stolen money).

On Standoff cyberbattle and other contests
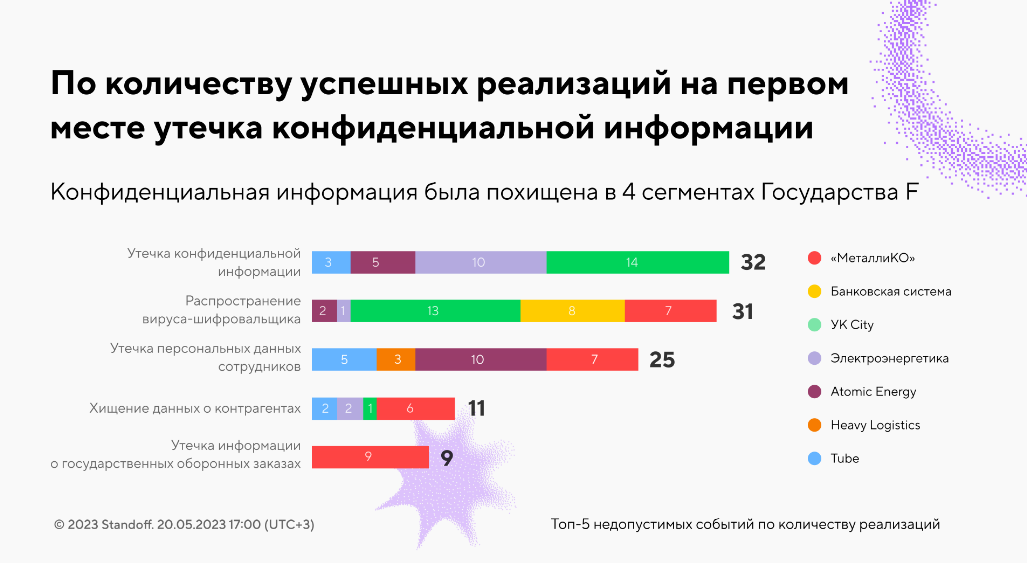
During the four-day-long cyberbattle, the attackers succeeded to trigger 204 non-tolerable events across the economy sectors simulated within the cyberrange. Out of 148 unique non-tolerable events, 64 were triggered. The team Codeby—now the only four-time cyberbattle winner—bagged the most events. No segment could withstand the red teams' onslaught. The most triggered events were "Leak of confidential information" (32 times) and "Ransomware infection" (31 times). The maximum number of successful hits were on Banking System (44) and City Housing & Utilities (44), with MetalliKO in third place (37), and Atomic Energy bringing up the rear (27).
During the cyberbattle that raged in State F, the attackers submitted 209 vulnerability reports, including 58% on critical, 24% on high, and 17% on medium risk level vulnerabilities. Remote Code Execution (RCE) ended up as the most popular type of detected vulnerability.
The defenders submitted 667 incident reports, mostly in the Tube segment (37%), and investigated 43 attacks.
Codeby finished first among the attack teams with a total of 193,454 points, True0xA3 came in second (143,264 points), and Bulba Hackers third (58,796 points).
The cyberfest featured a rich program of contests. In IDS Bypass, the contestants were testing out network defenses; while $natch was about hacking an ATM, a mobile bank, and a cash register. By the way, the latter was cracked open at least five times.

Around 10 players tried their hand at the difficult contest dubbed ETHical Hacking. They were taken through a number of challenges to hack smart contracts in the Ethereum network: by withdrawing all money from a smart contract or by setting the flag (contract's Boolean state variable value) to "true," depending on challenge description. Six guys passed through at least one challenge.
We are going to cover the results of all the contests in our additional materials: stand by for news and reports on individual cyberfest events. Lectures, sessions, contests, and competitions were aired online on PHDays website. Videos for most of the presentations will be published later. Follow the news on our website.
