The last two days also included 15 talks given by information security experts
Disaster has struck the cyber-range at
A hot day at the factory
Red team back2oaz continued their attack on the Nuft petrochemical plant. This time, they gained access to the plant control system, allowing them to close off the inlet valve to the refrigeration circuit. This led to overheating and disrupted the plant's chemical production processes. But the attack didn't end there—soon back2oaz succeeded in completely immobilizing the production process. Were this attack conducted on a real petrochemical plant, and not just in the mock-city of the cyber-range, the situation could lead to the injury and death of factory workers, as well as to toxic spills causing environmental pollution.
Attackers once again compromised the systems of the airport in Heavy Ship Logistics: team Hack.ERS succeeded in breaking into the system and making away with passengers' personal data.
On Friday night, the blue teams submitted 17 reports on registered incidents. A third were attacks on web applications. The defenders managed to submit 4 reports on incident investigations. On average, blue teams have required nine hours to investigate detected incidents. Earlier this week, the defenders of the business center were the first blue team to submit an incident investigation report, which cataloged the deletion of fines and damages data from the center's computer system. The team took additional time to investigate the incident in detail and understand how each of the two red teams conducted their attacks. It's certainly no easy task to sort out the details of two attacks that took place at practically the same time!
On the second day of the event, red teams submitted 63 reports on identified vulnerabilities. They found the greatest number of vulnerabilities in the systems of the companies Nuft and Big Bro Group.

The following night leading into Sunday morning, the city's bank was attacked twice. Team DeteAct obtained client card information and transferred money from those cards into their own account. It took the bank's defenders 3 hours and 26 minutes to investigate the incident. Soon after, team SPbCTF lifted the personal data of bank employees from the bank's internal ERP system. This data included employees' full names, phone numbers, email addresses, residential addresses, bank account numbers, and information regarding their positions and salaries. The blue team managed to investigate the incident in record time, taking only 2 hours and 57 minutes.
An interesting fact: one of the red teams conducting a sociotechnical attack by calling the remote banking system technical support. As a result, they succeeded in obtaining the personal data of one of the bank's clients.
The mock-city's billboards also didn't make it through the past two days unscathed: team SPbCTF gained access to the system for managing ad displays and were able to insert their own content in place of sanctioned material.
Nuft (the petrochemical sector) again suffered several attacks. Team back2oaz managed to disable the company's oil extraction equipment, immobilizing the oil extraction process. Meanwhile, team codeby.net succeeded in interfering with petrochemical production. As a result, yet another emergency was triggered at the petrochemical plant, halting production entirely.
Members of red teams DeteAct and codeby.net then set their sights on the IT systems of the 25 Hours amusement park. By hacking the database of the site for ticket sales, they made it impossible for park attendees to purchase tickets online. A dolorous day indeed!
Meanwhile, blue teams submitted another 32 reports on detected attacks. Most were in the offices of Heavy Ship Logistics (the airport) and Tube (TV and radio broadcasting). The defenders also conducted 4 more incident investigations. So far, the bank's team has proved to be the fastest at assembling investigation reports, averaging only about three hours per report.
Attacks on image recognition systems and the impact of COVID-19
Renowned information security specialist Sergey Gordeychik gave a presentation on vulnerabilities in machine learning infrastructure. Sergey shared practical security research results regarding components of artificial intelligence (AI) infrastructure, including NVIDIA DGX GPU servers, PyTorch, Keras, and TensorFlow machine learning frameworks, data streaming pipelines, and special applications. He especially focused on the topics of medical imaging and hidden cameras with face recognition capabilities.
Gordeychik observed that just because someone is a great AI researcher does not mean they know what's what in information security. The unfortunate result is that the AI security remains poorly understood, and attackers don't have to look far to find opportunities to attack AI systems. Gordeychik notes that the infrastructure components on which AI systems are built also make viable targets. In his talk, Gordeychik also presented the Grinder Framework tool, which can be used to conduct research on AI security.
The topic of image recognition was continued in the presentation of John Bambenek, president of Bambenek Labs. His talk was titled, "Adversarial machine learning and its impacts on cybersecurity." Bambenek illustrated how an attacker may mislead image classification systems via adversarial machine learning, and also how adversarial machine learning may actually be used to aid information security. Bambanek illuminated his talk with examples of methods that deceive classification systems, and suggested other methods to protect against such attacks.
Speaking on the shortcomings of machine learning today, Bambenek advised "creating models that are undefined" and not allowing machines to make their own decisions: "we can't remove people from the decision-making process—it is imperative that they conduct marking and strengthen the models. Ten percent of decisions should be made by 'hunt teams' to track ambiguous results."
BI.ZONE developer Maria Nedyak followed, presenting the results of a security study on one of today's key medical imaging standards, DICOM. Medical imaging systems are currently developing rapidly. Current approaches to medical imaging are based on the assumption that AI and machine learning systems can accept medical research data in DICOM format to conduct further analyses.
However, if an attacker manages to exploit vulnerabilities in the DICOM protocol, they will be able to deceive the imaging system. The results can be disastrous. For instance, a system analyzing lung scans for COVID-19 will produce incorrect data, patients will be misinformed regarding their infection status, and may consequently infect other people. Nediak spoke about the most interesting vulnerabilities in the DICOM ecosystem and demonstrated how easily and quickly we are actually able to detect vulnerabilities and eliminate them.
The COVID-19 pandemic has dramatically altered the threat landscape that we face. This was the message of Muslim Koser, founder and head of product and technology development at Volon. Among the threats that Koser discussed, he paid particular attention to attacks conducted on VPN companies with the aim of subsequently selling off VPN access on the dark web. He also spoke about the unprecedented increase in ransomware attacks that we have recently witnessed. Koser urged his listeners to protect their systems against the following ransomware: Revil, Nephilim, Net Walker, DoppelPaymer, Ryuk, Maze, Zeppelin, and Thanos. Koser noted that all these programs have become particularly active in recent months. He went on to note that targeted attacks have increasingly made use of open source utilities over the last nine months. He also alerted his audience to the fact that hackers have repurposed many types of malware for targeted attacks.
Koser urged companies to actively promote cybersecurity among their staff, to talk about attack vectors, and to model phishing campaigns and conduct analysis on the results. Koser also drew attention to the importance of prioritizing vulnerabilities and conducting regular penetration testing on IT systems.
How to protect your company from Lazarus and not lose your honeypots
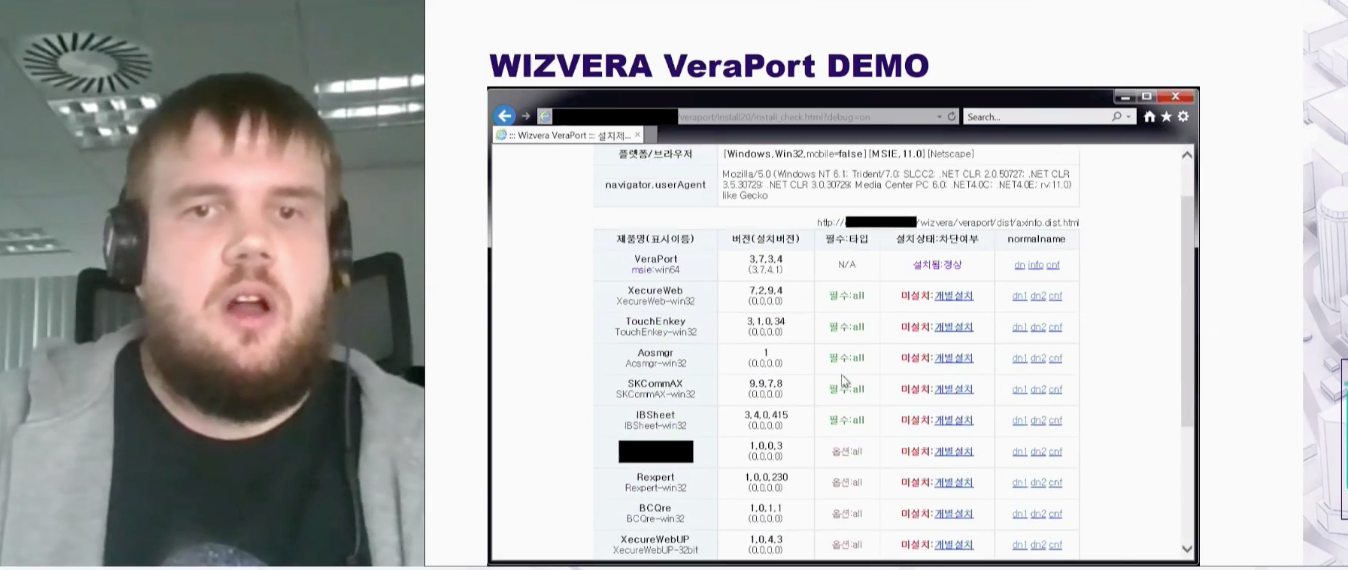
In supply chain attacks, hackers exploit their victims' trust in third-party organizations. A notable example is the NotPetya attack. In this attack, hackers gained access to a legitimate update server for M.E.Doc software (M.E.Doc is used for report and document management in accounting). As a result, many companies downloaded infected updates. ESET security researcher Anton Cherepanov and ESET virus analyst Peter Kálnai discussed a new malware campaign being rolled out by the hacker group known as Lazarus that takes this approach. In Lazarus's version of the attack, the trusted software that is infected is the application Wizvera Vera Port.
To avoid falling prey to Lazarus, Cherepanov and Kálnai recommend conducting IS reviews of software and service providers, assembling application whitelists, and using IS programs and organizational solutions that have been tested and verified.
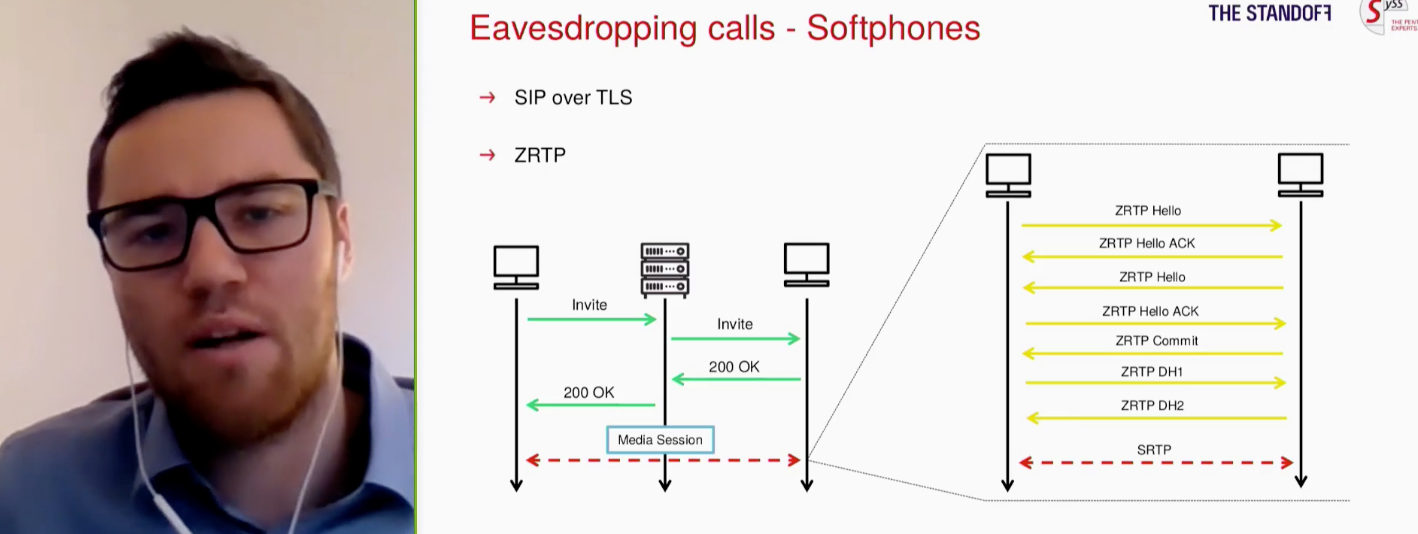
The COVID-19 pandemic has transformed programs for video conferencing and IP telephony into central elements of the corporate environment. Unfortunately, these communication channels are all too often plagued with security issues, states Moritz Abrell, an IT security consultant at SySS GmbH. Even monolithic corporate giants are still making heinous slip-ups in their IT security. It was only after several data-leak scandals that Zoom implemented end-to-end data encryption, and now Microsoft Teams is facing the same problem: Abrell noted that Microsoft Teams does not use end-to-end encryption, and instead directs private keys to Microsoft servers. He then gave a demonstration of his independently developed, open-source suite of tools for conducting penetration testing on voice-over-IP (VoIP) systems. To improve the security of IP telephony, Abrell suggested that his audience not trust manufacturer encryption and should conduct penetration tests on VoIP infrastructure and unified communications (UC). This includes messengers, video conference platforms, and speech recognition systems.
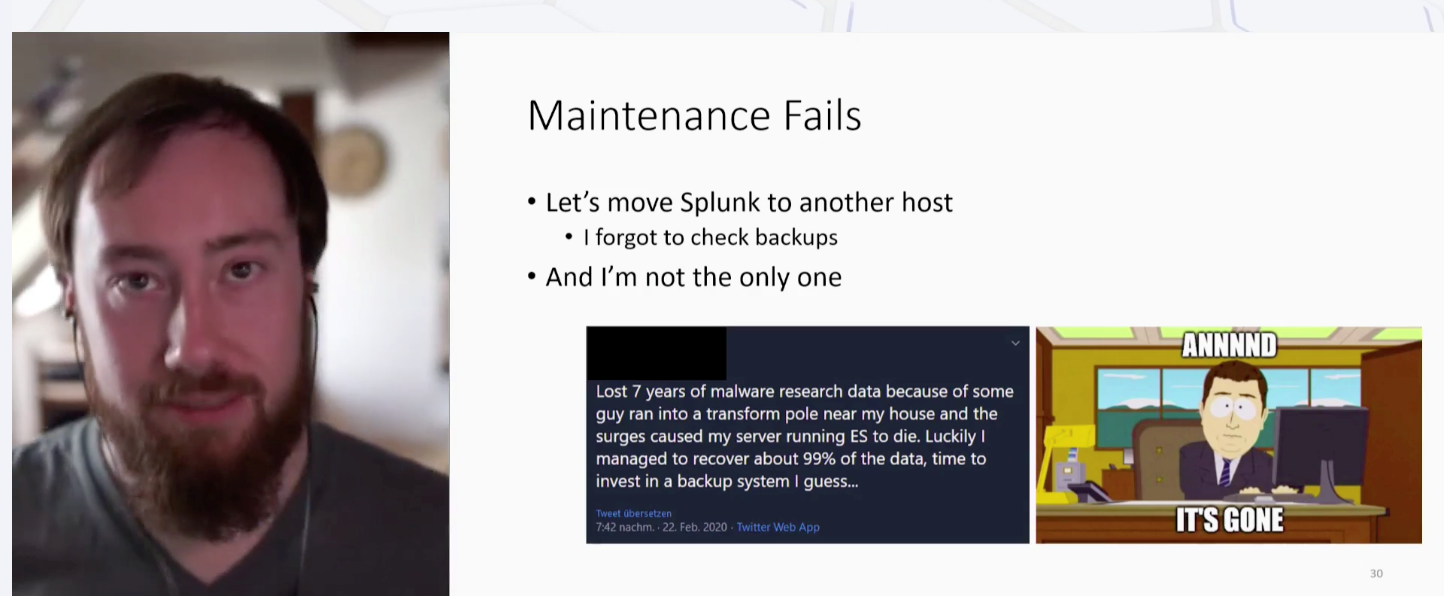
Traps designed to lure and deceive hackers, best known as honeypots, can be a valuable source of threat data. In his report, "Honey, I automated the pots! Honeypot infrastructure and automation," Matthias Meidinger, a software engineer at VMRay, stated that correctly deploying honeypots can be far from easy, as can be correctly interpreting the actions that they register. Meidinger advised his audience not to implement honeypots with root access, as hackers may break the traps. Instead, he recommended choosing trusted host providers. Providers who offer great terms, but who ask for a large down payment, are liable to disappear into thin air, taking the delicious honeypots with them. Once, when transferring Splunk to another host, Meidinger himself absentmindedly forgot to check his backups and ended up losing his saved data. In this he is far from alone: Meidinger gave another example of a researcher who almost lost the results of seven years of research when a teenager crashed into a transformer pole near his house, damaging the security specialist's ES server.
Trend Micro researchers Vladimir Kropotov and Fyodor Yarochkin gave a presentation on methodology for research of bulletproof hosting and on the principles of network indicator attribution. Bulletproof hosting services are used to create control servers, deliver payloads and exploits, and to host phishing pages and other components of attackers' network infrastructure. Attackers typically purchase access to these systems when preparing for an attack.
The speakers presented practical case studies of bulletproof fast-flux hosting, hosting on compromised infrastructure elements and dedicated servers, and other hosting strategies.
On Saturday and Sunday, Vyacheslav Moskvin, senior specialist in ICS security at Positive Technologies, continued to lead his workshop, "How to break a factory." Workshop participants learned about the main components of modern automated process control systems and the threats they face. Moskvin described the components' weak points from the perspective of pentesting, going into great detail, and illuminated typical attack vectors.
Moskvin notes, "There's good reason why they say that to hack an automated process control system, all you need to do is read the documentation." He continued, "That's why typical attack vectors on production automation systems abuse existing documented, and undocumented, functions." Moskvin noted that it is frequently possible to gain full control over critical industrial equipment simply by connecting to the equipment using the engineering software.
Numerous vulnerabilities in systems can further facilitate the work of attackers.
The Standoff is now approaching its climax—the event will reach its end on November 17! Stay tuned into key events and presentations from information security experts at standoff365.com or on Twitter, LinkedIn, Facebook, and YouTube.
