Introduction
During an investigation, Positive Technologies Expert Security Center (PT ESC) discovered a hacking toolkit that used the Telegram messaging app to manage backdoors. To penetrate the network and move laterally within it, attackers used both known malware, such as Impacket, Mimikatz, and network traffic tunneling tools (Chisel1, dnscat22, Gost3, and others), and new, less widespread malware, such as remote access Trojans that use Telegram API to download data. Malware analysis was performed by the cyberthreat research team (PT ESC).
TgRAT dropper
At the first stage, the dropper checks the parameters (arguments) used for its launch: this impacts the intermediate persistence stage. If there are input arguments, the add_payload stage begins (named after the function that performs it). If there are none, initialization and persistence occur. The dropper then:
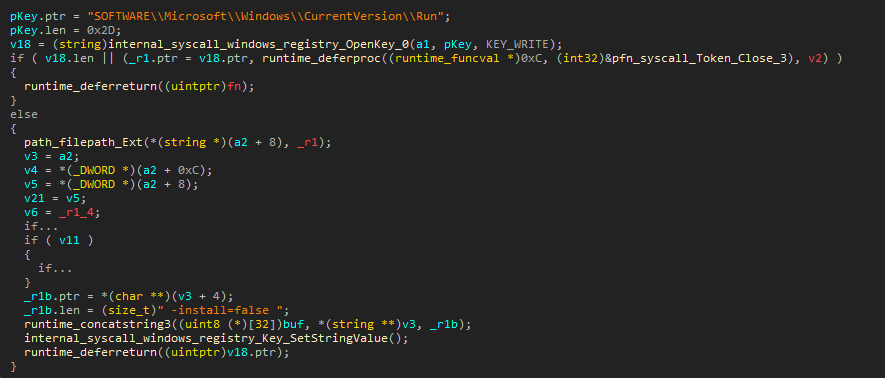
- Installs itself during startup with the " -install=false " parameter (Figure 1).
- Forms the name of the file with the payload (parses the path and the name of the current process, modifies this path and substitutes the name of the payload embedded in code).
- Decrypts the binary data contained in the program body using the AES algorithm in CTR mode (the initialization vector is embedded in the program body).
- Writes the decrypted data to the file and transfers control to the payload.
TgRAT backdoor
The payload file is a small RAT using Telegram as a C2 server. The server is a private Telegram chat, and the communication happens using Telegram API (github.com/wrwrabbit/telegram-bot-api-go library). We observed several modifications of this malware that differ in architecture; nevertheless, their functionality is the same.
At the very beginning, the RAT checks the name of the host on which it is running. If the name does not match the value embedded in the program body, the malware stops. It is clear that the malware was developed specifically for specific computers.
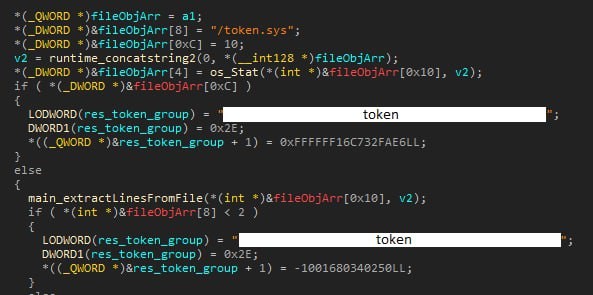
The token and the communication chat ID can be read from the token.sys file, which is supposed to be in the same directory as the malware. If there is no file, the malware uses the token and ID embedded in the code (Figure 2).
After the connection is established, the malware obtains the command names and arguments (if necessary).
The format of storing and executing commands is particularly interesting. During the initialization of parameters, variables, and libraries, the malware forms a structure of specific data, identical to a/the map (Figure 3).
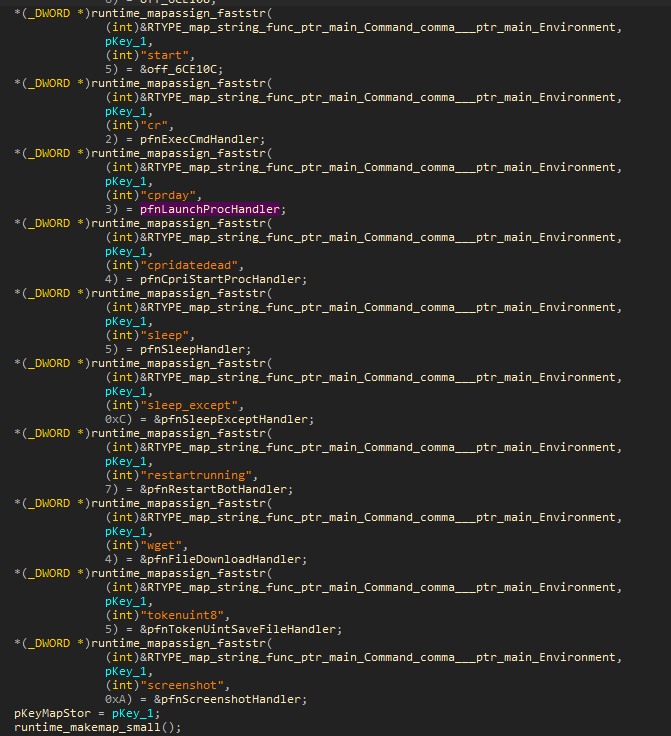
In addition to service fields, this structure stores pointers to the functions that will be used for command execution. The structure is used to map the command name that comes from the C2 server (Telegram chat) to the function.
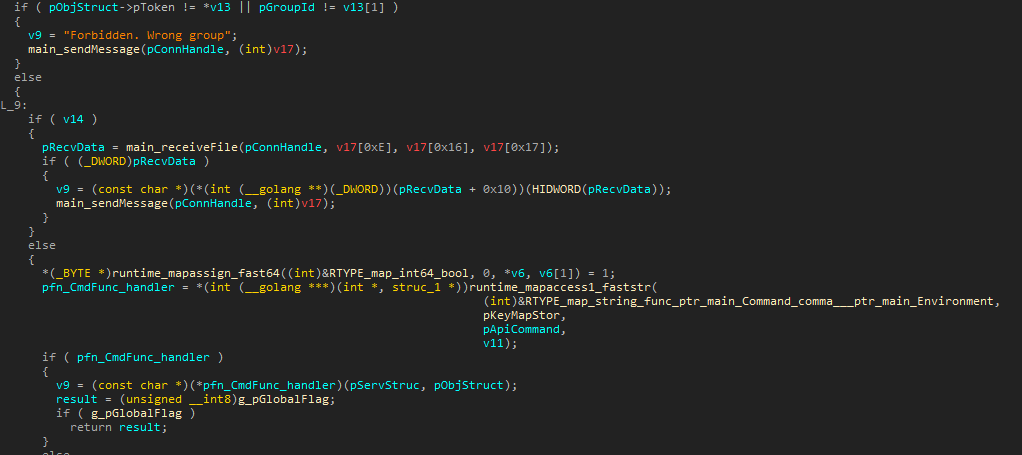
The malware receives the command name and then, using methods of accessing the structure described above, gets the address of the handler function (the pfn_CmdFunc_handler variable in Figure 4). Next, the malware calls this function.
The analysis of the initialization code of the structure containing the addresses of functions and their names made it much easier to identify the types of commands executed by the malware, including:
- Obtaining the information about the infected computer (see Figure 5)
- Connection (bind) to a particular Telegram chat; connection error message
- Self-termination (kill <PID>)
- Saving a message as a file
- Self-updating
- Shell launch
- Executing the command in the shell and saving the result as a file
- Starting a process
- Sleep during a certain time
- Bot reset
- File download
- Taking a screenshot

Conclusions
Even though hackers use legitimate protocols to manage their tools and load data, this attack can be easily detected with minimal traffic monitoring. To protect against this attack, it is necessary to:
- Protect all hosts, including servers, with antivirus software: hackers continue to use common tools that any antivirus tool can easily handle.
- Monitor traffic from the servers on the Internet at the perimeter. In most infrastructures, traffic transfer from internal servers to Telegram servers is suspicious.
- Monitor traffic within the network. This will enable you to identify network tunnels and unusual communication between the servers.
